Identity verification has turned into a vital tool to detect and prevent fraud in every industry, and telecommunication is no exception. While the industry struggles with several identity threats, including vishing calls, account takeovers, call transfer fraud, etc. Fortunately, such risks can be minimized to a great extent using a robust identity verification solution.
You will be surprised to know that the history of telecommunication started with smoke signals and drums. The year 1790 was the 1st time when a fixed semaphore system came into appearance in Europe. Until 1830, there was no fixed telecommunication system like we see today.
Today, telecommunication is one of the largest and fastest-growing industries in the world. Numerous telecom companies worldwide provide voice, video, text, and internet data services. According to recent statistics, the global telecom service market was valued at 1.74 trillion USD.
While the telecommunication industry has a significant role in every sector and is growing rapidly, it has some challenges. Identity fraud is one of the most common threats to the industry. According to the survey conducted by Global CFCA in 2015, identity fraud represents approximately 35% of all frauds in the telecom industry.
In this blog post, we’ll examine the role of identity verification in the telecommunication industry. But before that, let’s examine some common fraud types in the telecom sector.
What are the Key Fraud Types in Telecommunication?
Telecommunication fraud involves illegally acquiring sensitive information, such as ID card numbers or bank account info, from service providers or their customers via telecommunications services. Additionally, identity theft is a severe concern in the telecom industry; mobile telecommunication is especially affected.
As per the Cifas reporting, the industry’s identity fraud rate increased by 50% in 2017. Another report of the Organized Crime and Corruption Reporting Project (OCCRP) claims that the telecom frauds cause the loss of around 32.7 billion US dollars to the world annually. The report further says that fraudsters hack the telecommunication system to abuse legitimate enterprises for criminal gain.
The battle against fraud in this industry seems unending, and the importance of risk awareness, along with investment in automated digital identity verification systems, will continue to be critical in the coming years.
Here is a short list of the most common fraud types in the telecom industry right now:
1. Vishing Calls
It is a typical phone scam in which fraudsters trick people into revealing their personal and financial information to transfer money. During the phone call, the criminal uses social engineering (psychological manipulation) to get victims to share their personal information and financial details.
Fraudsters might claim to be a bank representative or law enforcement officer and tell you that your account has been compromised. They might even ask you to install software that is actually Malware.
Some of the common vishing scams include:
- Compromised bank or credit card accounts.
- Loan or investment scams.
- Tax revenue scams.
2. Call Transfer Fraud
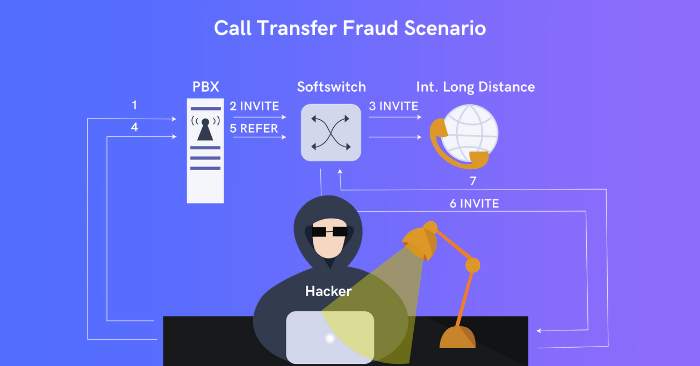
The technology has enabled fraudsters to use various fraud techniques and call transfer fraud. This type of fraud happens when a fraudster hacks a VoIP PBX to make free international calls. VoIP stands for ‘Voice over Internet Protocol.’ In your private phone system, the switchboard function is handled by the PBX, which stands for ‘Private Branch Exchange.’ An IP PBX system is the core component of most contemporary VoIP phone systems.
With the help of a compromised PBX, a hacker transfers the call to their own phone. Thus, they can speak with anyone via a hacked soft switch without getting into the telecom operator’s notice. Since there is no way of tracking a call once it is transferred out of the network, fraudsters can extort or blackmail without getting tracked.
See the following diagram to understand the call transfer fraud scenario.
3. Account Takeover
Account takeover happens when a malicious third-party gains access to a user’s account credentials. In Europe, most telecom companies provide their customers with the opportunity to buy a high-value device on monthly installments. Unfortunately, this business model has been proving beneficial for fraudsters as well. They steal customers’ account details and use that information to buy expensive devices, which they immediately sell-off and leave the victim with the bill.
Mobile telecom is at high risk of account takeover threat. In 2016, the UK Company TalkTalk was hit with a £400,000 fine for the cyberattack that exposed the personal details of more than 150,000 customers to cybercriminals.
4. Romance Fraud
Romance fraud happens when a fraudster adopts a fake online identity to gain a victim’s trust. However, romance fraud in the telecommunication industry is a bit different. Generally, it involves convincing the victim to share their account details to buy an expensive device.
In 2023, individuals aged 55 to 64 years lost the most money to romance scams, totaling over $10 million. However, the highest number of scam reports came from those aged 35 to 44 years.
Romance scams happen when a criminal creates a fake online persona to earn a victim’s affection and trust. The scammer then exploits the illusion of a romantic or intimate relationship to manipulate and steal from the victim.
Why is Identity Verification in the Telecom Industry Important?
The role of identity verification in the telecommunication industry is exceptionally crucial. It keeps fraud at bay by verifying the authenticity of the documents customers provide.
A proper identity verification system helps a telecom company authenticate its customers and ensures the holder is the rightful owner. It also enables telecom operators to evaluate the risk associated with customers via different checks.
For example, Perpetual KYC, or pKYC, modernizes the traditional Know Your Customer (KYC) process used by banks and financial institutions to verify customer identities. pKYC software can enhance the onboarding process across various industries by doing away with paper-based methods and record-keeping, enabling businesses to connect with customers who may be located remotely. Moreover, when combined with selfie biometrics, pKYC solutions can greatly improve the accuracy and efficiency of customer identification processes.
What are the Benefits of ID Verification for Telecom Companies?
A robust, fully streamlined ID verification process is beneficial for telecom companies. It helps prevent money laundering and other crimes since the telecommunication industry is common among fraudsters due to its eSIM and other services, which are tools for bad actors to commit further crimes.
It also brings stability and enables telecom platforms to increase their profits, among other perks that we break down below:
Ensured KYC Compliance
Whether it is in-person onboarding or digital onboarding, identity verification plays an important role in identifying and preventing fraudulent activities that put telecom operators at risk.
Using real-time biometric facial recognition solutions, telecom operators can obtain authentic identification documentation of customers and create a safe environment for both the customer and the company.
Since advanced identity verification solutions help telecom companies run a background check on users, they can easily comply with KYC and anti-money laundering (AML) compliance regulations
Protected Reputation
Trust is more important than ever before for telecommunication companies because users nowadays look for operators to rely on. Identity frauds not only cause financial penalties but also lead to a loss of reputation.
Better Customer Experience
A robust identity verification system also allows telecom operators to improve the overall experience for their customers. Since customers’ onboarding journey becomes frictionless, they feel confident about their relationship with a telecom company.
In general, identity verification solutions for the telecom industry help companies:
- Reduce identity fraud.
- Comply with KYC, AML, and other security regulations.
- Minimize onboarding costs.
- Improve the overall customer experience.
- Protect brand reputation.
There are so many benefits of an identity verification solution for the telecommunication industry, so why not implement it?
iDenfy is a renowned identity verification solution provider in Lithuania that offers a robust, AI-enabled identity verification system that combines face recognition, liveness detection, and ID verification.
Get started right away.
This blog post was updated on the 3rd of July, 2024, to reflect the latest insights.