Rarely can businesses be safe from data breaches, ever-changing threats, and significantly raised expectations from regulatory bodies. Working harder to earn and maintain trust is necessary now more than before for an organization. Information security certifications and attestations have increasingly become critical tools here. Two of the most widely recognized are SOC 2 and ISO 27001.
Both certifications enable an organization to guard sensitive information, demonstrate responsibility, and handle the question of security governance quite differently. Knowing their differences, strengths, and intended audiences can help organizations in a more appropriate and strategic security program.
What is SOC 2?
SOC 2, also known as System and Organization Controls 2, was developed by the American Institute of Certified Public Accountants (AICPA), finding its origin to assure customers and regulators worldwide that an organization’s processes and controls meet a minimum of data protection and operational integrity standards. This auditing procedure focuses mainly on nonfinancial controls relevant to information security, privacy, processing integrity, availability, and confidentiality — collectively known as the Trust Services Criteria (TSC).
SOC 2 reports are of two types:
- Type I assesses the design of your controls, which means a snapshot that shows the proper safeguards are in place.
- Type II takes one step further by measuring how controls operate in real-time over a set period, generally several months.
Many organizations start with a SOC 2 Type I engagement to build preliminary credibility and then pursue a Type II audit to prove operational maturity.
What is ISO 27001?
ISO 27001 is an international standard and a choice for organizations working globally or serving clients in different regions. A certificate recognized by a reputable certifying body can ease compliance with most kinds of regulations and help third parties ensure that you apply a proven, reliable, evolving standard internationally.
The standard for regulating such controls is through the joint efforts of the industry’s prominent and well-recognized organizations: the ISO and the IEC (International Organization for Standardization). ISO 27001 goes beyond focusing on any specific state of controls at a given point and requires establishing a comprehensive Information Security Management System (ISMS). Often, it provides a directly structured blueprint from which organizations can identify their security controls, governance practices, risk management policies, and incident response procedures and continually improve.
An organization can acquire ISO 27001 certification through an accredited certification body. It typically starts with gap analysis, ISMS development, policy and procedure documentation, and internal audits. At the end, an independent auditor performs a two-stage assessment:
- Stage 1: Reviewing documentation.
- Stage 2: Verifying the implementation and effectiveness of your ISMS.
By being successful, an auditor will provide the organization with an ISO 27001 Certificate valid for three years; regular surveillance audits are necessary to ensure that continuity in improvement and compliance is still here.
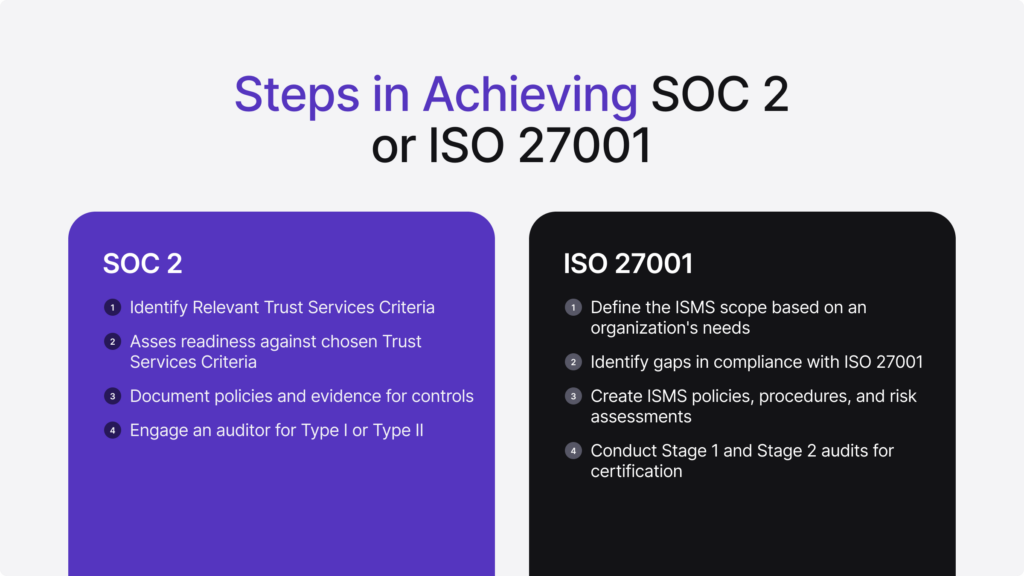
Key Differences Between SOC 2 and ISO 27001
SOC 2 and ISO 27001 are trust-building and reinforcement strategies in data security, but their methodology differs based on several key areas:
1. Attestation and Certification
SOC 2 provides third-party assurance that an auditor prepared and tested your controls in place. It does not assure formal certification but distributes a three-part report to interested parties. ISO 27001, on the other hand, leads to a globally recognized independent certification with a formal standard attached to it. An organization can display this certificate for all to see and use as proof of rigorous adherence and commitment to continuous processes.
2. Management Controls
SOC 2 focuses more on specific controls concerning the Trust Services Criteria. It needs to be more prescriptive, and its idea is to show if these checks are reliable, especially on security, and work just as somebody would have thought. The more generalized approach adopted by ISO 27001 demands the incorporation of an ISMS through policies, procedures, training, risk assessment, and continuous evaluation.
The ISO 27001 variant mostly kicks off a cycle where it can do various things based on aspects such as the Plan-Do-Check-Act model, which can advance your security posture within those showing change.
3. Market and Geographical Expectations
SOC 2 is one of the most anticipated frameworks in North America; ISO 27001 enjoys widespread international recognition and provides a strategic differentiator if someone’s organization does business globally; some industries, especially throughout Europe and Asia, enjoy the internationally standardized, certification-based approach of ISO 27001 more.
4. Criteria, Clauses, and Scope
With SOC 2, the organization identifies which TSC are in scope. Security, sometimes called Common Criteria, is the only required; Availability, Processing Integrity, Confidentiality, and Privacy are optional to be selectively addressed by a company about its unique risk profile and customer requirements. It gives flexibility but also requires clarity on what is in scope.
ISO 27001 relies neither on a “menu” approach to selecting a set of criteria nor simply on an approach that specifies one way to implement the principles. Instead, it outlines mandatory ISMS requirements, from risk assessment to leadership oversight and continuous improvement practices. Ultimately, it also refers to Annex A’s recommended set of controls (legal supplements that can both contribute to a contract or legal proceeding and stand alone as a source of information on a particular topic).
It covers domains ranging from asset management to cryptography, business continuity, and supplier relations. Organizations justify the controls in Annex A, to which they apply strict adherence to the risk-based approach.
5. Project Timelines, Costs, and Complexities
SOC 2 and ISO 27001 require efforts, resources, and investment; however, their paths slightly differ.
For SOC 2, assuming good baseline controls and documentation, many organizations can attain a Type I report in a few months. In general, Type II requires a more extended testing period of usually six to twelve months because the auditor has to verify that controls have been operating effectively through time. Costs depend upon the complexity of your environment, the number of controls tested, and the use of external consultants or automated compliance tools.
ISO 27001 certification may require an extended preparation phase. Establishing an appropriate ISMS may take six to eighteen months, depending on the complexity of an organization. Documentation, policy development, employee training, and internal audits are the steps that precede the external assessment.
The initial cost can be higher because the need for extensive process design is present, and changes in the organizational culture are probably needed to introduce a concept of continuous improvement. Once certified, maintaining ISO 27001 becomes a steady-state activity with predictable surveillance costs, and the organization benefits from an established mature security framework.
6. Ongoing Maintenance and Continuous Improvement
SOC 2 is often considered a snapshot of an organization’s security posture, especially for Type I engagements. While Type II covers a period, the outcome is still a report linked to a specific interval. For organizations to succeed in annual reassessments, they must maintain strong operational controls throughout the year, but SOC 2 itself does not drive a continuous improvement cycle. It’s more about passing the test of that particular moment or showing that your environment is stable and secure.
On the other hand, ISO 27001 calls for continuous improvement. The standard is here upon a life cycle in information security: identification of risk, implementation of controls, verification of effectiveness, and improvement. Auditors would return periodically to verify that ISMS remained in step with the standard and was maturing as the threat landscape continued to evolve.

Factors to Assess when Choosing SOC 2 or ISO 27001
Several factors come into consideration when an organization is deciding between SOC 2 and ISO 27001:
Geographic Footprint-Market Demand
US customers may still directly ask for the SOC 2 reports, whereas worldwide or international customers can use an ISO 27001 certificate much more smoothly. Consider where your customers are and what resonates with them.
Strategic goals and organizational culture
If your leadership thinks of information security as not a destination but a travel towards improvement and holistic risk management, the approach of the ISO 27001 set may be more natural. Considering the U.S. market, you only need to prove you hold a trusted baseline, and SOC 2 may be enough by itself.
Flexibility vs. Standardization
SOC 2 allows you to select which TSC you implement; it is customizable but requires you to be very specific about the scope. ISO 27001 requires an organized approach to cover a broad range of security aspects. If you prefer a well-defined, universally recognized standard, ISO 27001 may offer a more straightforward path.
Growth and Long-Term Planning
Various organizations start with SOC 2 to meet today’s customer requirements and transition that experience and control environment they’ve built to overcome ISO 27001. But, if you want to swim into international markets or solidify an enterprise-level compliance program, you can start with ISO 27001.
Maximizing the Value of Your Compliance Efforts
Use these frameworks as a starting point for ongoing risk management. Well beyond the audit or certification, continue refining your internal policies, strengthening controls, and encouraging a culture of security awareness. Keep tabs on how industry best practices evolve and integrate that knowledge into your ISMS or SOC 2 control set. A continuous improvement cycle will prepare you to handle ever-changing threats and grow client expectations.
Integration can be a means for an organization to get the “best of both worlds.” Aligning your ISMS with ISO 27001 and then scoping a SOC 2 report against the controls that matter most to your clients can create a powerful synergy.

Conclusion
In a world where anyone in the headlines can find keywords such as breaches, ransomware attacks, and data misuse, SOC 2 and ISO 27001 are the meaningful frameworks that add structure, credibility, and reassurance to your information security posture. Each plays a different role: SOC 2 provides flexible attestation according to the demands of the North American market, while ISO 27001 offers internationally recognized certification and forms a leading foundation for continuous, strategic security improvements.
Whether SOC 2, ISO 27001, or a combined approach is proper for your organization depends on what makes the most business sense in your singular environment, considering target markets. Adoption should consider the control, scope, market expectations, and resources. Whatever the choice, following any standardized framework is one influential word to your customers, regulators, and partners.
iDenfy has also recently received its SOC 2 attestation report and is ISO 27001-compliant. Our team is dedicated to maintaining the highest security standards while offering you various RegTech tools, which you can try out for free.




