If you think biometric face recognition systems are not vulnerable to spoofing attacks, you’re mistaken. Over the past few years, biometric face spoofing attacks have increased significantly all across the globe.
However, thankfully, we have liveness detection, which plays an extremely important role in identity verification by confirming the live presence of the individual, making it far more challenging for spoofers to impersonate someone else. What’s more, is that this technology enhances security while also improving the overall user experience in the authentication process.
In this post, we’re going in-depth regarding liveness detection techniques to help you prevent spoofing attacks and presentation attacks (PA).
What is a Spoofing Attack?

For those who don’t know, a spoofing attack is when a cybercriminal tries to gain illegitimate access to someone else’s rights through a photo, video, or other material for an authorized person’s face. If the attempt succeeds, the scam artist gains the rights of another person.
A spoofing attack is a fraudulent act of hiding your identity or disguising another form of communication to appear as a legitimate and trusted source. In the context of Know Your Customer (KYC) verification, this is a common tactic used by bad actors to bypass the identity verification check, which often happens during the account opening process on environments like a banking app or an iGaming site. Other popular types of spoofing include email spoofing in phishing campaigns and caller ID spoofing.
Spoofing attacks often exploit trust by pretending to be a familiar person or organization known to the victim. In certain scenarios, like phishing with website spoofing, these fraudulent messages may even be customized to the victim’s identity, aiming to deceive them into thinking the communication is genuine. When users are unaware of the scam, they become vulnerable to falling victim to a spoofing attack.
There are numerous ways hackers can execute face spoofing attacks. Let’s have a look at some common methods below.
Classifications of a Spoofing Attack

Most of the face spoofing attacks come under the category of presentation attacks. Such attacks involve using 2D and 3D — statistic or dynamic — objects to deceive facial recognition software:
- 2D Presentation Attacks: Static 2D attacks are conducted using facial masks, photographs, or flat paper, while dynamic versions use multiple pictures in a sequence or screen video replays.
- 3D Presentation Attacks: In 3D static presentation attacks, cybercriminals use 3D prints and sculptures, whereas, in dynamic versions, they use advanced robots to fool face recognition solutions.
Of course, these are not the only methods spoofers use. Presentation attacks are evolving with technology. However, due to technological limitations, 2D attacks are comparatively widespread.
It’s true that face recognition systems can easily be exposed to spoofing attacks; it doesn’t mean you can’t do anything to prevent them. Some biometric liveness checks can help you fight against hacking attempts.
And now, let’s get to know about some techniques to prevent face recognition spoofing.
How to Prevent a Spoofing Attack with Liveness Detection?
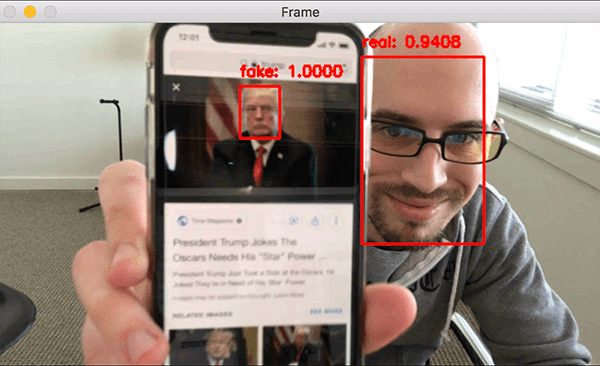
There are various methods to counter face spoof attacks. They all come under the general term of “liveness detection.”
Liveness detection is a process used to identify non-living spoofs, such as photos, prints, or masks, ensuring the person in a selfie is real. This is a common technique used in biometric authentication or selfie verification. For regulated industries like banks, this is a mandatory KYC procedure, often combined with another KYC measure, document verification. What’s good about liveness detection technology is that it runs in the background after submission, using advanced algorithms. Liveness checks deter fraudsters or reveal mismatches with uploaded ID documents.
Liveness detection aims to identify if a face is alive or created by cybercrooks. In short, the technology detects the difference between a real face and a replica. That said, there are two major approaches when it comes to liveness detection, known as active and passive liveness detection. The active approach needs users to evidence their “liveness” by communicating with a face recognition system. On the contrary, passive liveness detection is hidden from the end-user and doesn’t need any action on its side.
The difference between active and passive liveness checks is user involvement. Active checks require users to perform specific actions to prove their live presence, while passive checks do not rely on user participation and aim to detect liveness through automated analysis.
We go into more detail below:
🟢 Active Liveness Detection
As mentioned above, active face liveness detection is an interactive approach to detect fraud; users have to stand in front of a camera and perform certain actions to demonstrate their rights or privileges with the system.
For example, these actions could be a smile, nod, blink, etc. In some cases, these actions could be randomized to add an extra layer of security to the system. Users won’t be able to gain access until they don’t complete all the required actions.
The choice between active and passive liveness checks depends on the specific use case and the balance between security and user experience. Active checks are often preferred when a higher level of security is required, while passive checks may be more suitable for applications where user convenience is a priority.
🟢 Passive Liveness Detection
In some cases, passive liveness detection proves a convenient protection option. Passive liveness checks are designed to be less intrusive and more user-friendly since users do not need to perform any actions. They aim to detect liveness while minimizing user interaction.
With this type of detection, there is no way for users to find out that they are being tested. The detection devices manage everything on their own. In general, passive liveness checks use advanced algorithms and sensors to analyze various biometric data, such as facial movements, thermal signatures, or even pulse detection, without any explicit user involvement.
Top 5 Anti-Spoofing Techniques

Now it’s clear that face detection systems based on 2D and 3D images are vulnerable to spoofing attacks. However, it’s also true that such attacks can be prevented using liveness detection techniques based on texture, motion, shape, color, or reflectance.
Check out some popular liveness detection techniques below:
1. Eye Blink Detection
Eye blink detection has the highest accuracy. Natural eye blinking is a straightforward way to find out whether or not a face is live. The average human being blinks 15 to 30 times every minute, and eyes stay shut for approximately 250 milliseconds during a blink.
The modern, state-of-the-art cameras are capable of recording videos with far smaller intervals between frames. Consequently, eye blink detection implementation can help you identify and prevent possible presentation attacks. Deep learning can be added to this technique to enhance its effectiveness.
2. Deep Learning
It is another effective solution that can help you with anti-spoofing. A convolutional neural network or CNN can be trained to determine the difference between real and spoofed photos. Already a lot of businesses have brought this technology into use to protect their systems.
3. Challenge-Response Technique
A challenge-response system validates the identity of a user based on a series of challenges, such as head movements, smiles, and facial expressions of happiness and sadness.
4. 3D Cameras
3D Cameras are considered one of the most reliable techniques to prevent spoofing techniques. These cameras can determine the difference between a face and a flat shape. Therefore, they provide high accuracy against presentation attacks.
5. Active Flash
Active Flash reduces the risk of presentation attacks by enabling us to identify spoofing using the reflections of light on a face. It involves using a changing light environment offered by the extra light that comes from a device’s screen. The white light gives sufficient facial reflection.
What Else Can You Expect Next for Anti-Spoofing Technology?

There is much more you can expect from liveness detection technologies in the coming years. With the combined use of artificial intelligence and deep learning, face anti-spoofing technology can be made more robust and effective. At iDenfy, we understand that you want the most accurate KYC checks with a focus on user experience.
And, for that, we have used automation to create a complete RegTech suite: automated ID verification solutions (with active and passive liveness checks, customer reverification options, etc.), including other solutions for ongoing due diligence, such as AML screening or automated customer risk assessment – both for individual clients and other companies.
Let’s chat so we could show you around our dashboard for a more hands-on approach.