Not too long ago, the concept of paying for groceries with a simple tap of one electronic device to another would have sounded like a science fiction movie. Thanks to near-field communication (NFC) technology and the accompanying smart tags that make it an actual reality.
An NFC tag and its reader can establish wireless communication. Typically, the tag contains a certain amount of data, which the tag can transmit to the reader through electromagnetic pulses. These pulses represent 1s and 0s, enabling the reader to interpret the information stored on the tag.
An NFC tag is also a more secure alternative for a QR code in short-range applications, such as Apple Pay. Ultimately, the technology involves electronic reader devices that can retrieve data from NFC tags. That’s why NFC is called the ultimate connectivity tool — it enhances the capabilities of various devices, including smartphones, tablets, and payment cards.
In this blog post, we’ll explain how you can use an NFC tag in various scenarios, including for identity verification.
What Does an NFC Tag Do?
An NFC tag is a small electronic device that stores data and can wirelessly transmit that data to other NFC-enabled devices, typically through a simple touch or close proximity. These tags are used for different purposes, such as information sharing, identity verification, contactless payments, and task automation, making them versatile tools for providing users with convenience.
NFC tags also go by various names, including smart tags or info tags. However, their fundamental structure closely resembles RFID tags. Both types contain storage memory, along with a radio chip connected to an antenna.
What is RFID?
RFID technology, which stands for Radio-Frequency Identification, is a system that uses radio waves to identify, track, and manage various objects, people, or animals remotely. It has proven to be a successful anti-theft measure for tracking inventory across different industries, including manufacturing, healthcare, automotive, and apparel.
RFID systems consist of RFID tags (also known as RFID transponders) and RFID readers. Companies use them wherever there’s a requirement to monitor and manage items effectively.
Here’s how RFID works:
- RFID tag. It’s a small electronic device that contains a unique identifier and can store data. RFID tags come in various forms, including labels, cards, or even implanted chips. They can be passive (powered by the RFID reader’s radio waves) or active (with their own power source, like a battery).
- RFID reader. It’s a device that uses radio-frequency signals to communicate with another RFID tag. Readers send out radio waves, and when an RFID tag enters the reader’s range, it receives the signal, powers up, and sends its stored data back to the reader.
- Software. The data from the RFID readers is typically sent to a database or software system for processing and management. This helps companies to track and manage the tagged items, people, or animals efficiently.
What is Near-Field Communication (NFC)?
Near-Field Communication, or NFC, can be thought of as a blend of RFID and Bluetooth. Unlike RFID, NFC tags operate at a very close range, offering users greater precision. Additionally, NFC eliminates the need for manual device discovery and synchronization, a requirement in Bluetooth Low Energy (BLE) connections.
NFC-enabled devices have two categories, which include:
- Passive NFC devices. These are typically compact transmitters that don’t require a power source. They can send data to other NFC-enabled devices but lack the capability to process incoming data. For example, advertisements.
- Active NFC devices. These devices have the ability to both send and receive data. The most common example is a smartphone. Mobile wallets such as Apple Pay or Android Pay and similar contactless payment solutions also operate using NFC as their main technology.
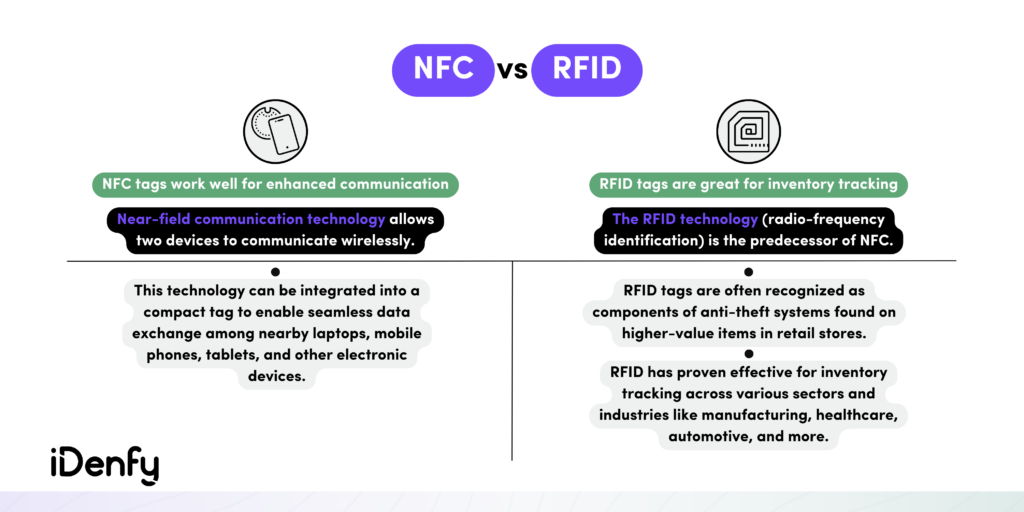
What’s the Difference Between NFC and RFID?
The difference between NFC and RFID lies in their communication methods. While NFC connectivity may appear similar to Bluetooth and Wi-Fi connections, the key distinction lies in how they transmit data. NFC relies on electromagnetic radio fields, whereas Bluetooth and Wi-Fi primarily use radio transmissions for communication.
Another difference is in how NFC tags are designed specifically for NFC systems. Their nature allows them to incorporate into a wide range of products easily. For example, items like the mentioned advertisements, stickers, ski lift passes, prescription bottles, and so on.
NFC-enabled smartphones can also act as an NFC tag. Different from RFID, which supports only one-way communication, NFC enables two-way data transfer. This means that a smartphone can emulate an embedded NFC tag, similar to the ones used for contactless payments.
NFC Tag Types
The NFC tag has various types. They are categorized into five subtypes, labeled as Type 1 through 5. Type 1 tags are the most basic and have limited capabilities, with the capacity to store less than one kilobyte of data. This translates to just a few hundred characters of text, sufficient for storing a Wi-Fi password or a URL, but not much more. That said, most NFC tags adhere to the ISO 14443 standard, which controls wireless and proximity-based data transmission.
In general, NFC tags differ in their memory capacity and reading speeds. Type 5 NFC tags have a memory capacity of 32KB, which is larger compared to Type 1 tags. They can also transmit data at a speed approximately four times faster than Type 1 tags. Unfortunately, an interesting comparison is that even with this capacity, Type 5 NFC tags still don’t match the storage capacity of a standard microSD card.
Can You Rewrite an NFC Tag?
An NFC tag is rewritable. However, it depends on the NFC tag type. NFC tags come in different types, including read-only and rewritable (read-write) varieties. Among the five types of NFC tags, types 1 to 3 are rewritable. Additionally, it’s possible to block them, preventing any further modifications.
Rewritable NFC tags can have their data altered or updated using an NFC-enabled device, such as a smartphone. This makes them versatile for various applications. For example, for updating product information, changing access permissions, or modifying stored data as needed.
How Exactly Do NFC Tags Work?
NFC tags operate similarly to other RFID tags by communicating using radio waves. That means in an NFC data exchange, two devices — the NFC tag and the NFC reader — exchange information. In other words, NFC tags derive power from the reading device using magnetic induction. Once the reader approaches, it activates the tag and initiates data transfer.
NFC technology operates within a short range, typically around 4 inches or 10 centimeters. NFC tags do not require a built-in battery. They are passive and draw power from another device, such as a smartphone. Additionally, an NFC reader establishes a connection with one NFC tag at a time, reducing the likelihood of accidental transactions.
What is an NFC Reader?
An NFC reader supplies power when reading data from passive NFC tags. To achieve this, NFC readers require their own power source to pass an electric current through a coil. This action generates an alternating magnetic field in the immediate vicinity of the reader. When an NFC tag is brought within the range of this magnetic field, the coupling occurs between the two coils.
NFC has been a feature on phones since as early as 2004. That means some phones had NFC capabilities before the iPhone was introduced. Despite that, the most commonly encountered NFC readers are found in contactless payment terminals, with public transport access gateways being a close second. In both scenarios, users are typically issued a unique NFC tag as a token, card, or mobile app.
What Does the NFC Payment Process Look Like?
In NFC payments, NFC chips exchange encrypted data. This means that card information can be securely stored on a smartphone, effectively turning it into a virtual card. This setup allows users to make convenient payments without carrying multiple physical cards in their wallets. All cards can be stored on users’ smartphones.
When paired with an antenna, the NFC chip creates a fully operational device. You’ve guessed it, it’s called an NFC tag. This antenna enables the chip to engage with an NFC reader, like a smartphone, by generating an electromagnetic field. NFC chips then utilize this field to facilitate wireless data communication.
What is the Difference Between an NFC Chip and an NFC Tag?
An NFC chip is an integrated circuit (IC) that enables a device, such as a smartphone or payment card, to communicate using NFC technology. An NFC tag, on the other hand, is a passive device that contains an NFC chip along with an antenna.
The difference is that an NFC chip is an active component embedded within devices, enabling them to interact with other NFC devices and tags, while an NFC tag is a passive device containing an NFC chip and antenna, used to store and transmit data when activated by an NFC reader or device.
What About NFC Identity Verification?
NFC identity verification is used to verify customer identities through chip-based identity documents. These documents incorporate RFID chips to store personal information, including details like name, address, date of birth, and sometimes even biometric data. NFC-enabled devices read RFID data, enabling NFC-based verification.
And what’s best about NFC identity verification is that it has two common elements: ID documents and smartphones. When an NFC-enabled device is tapped against the ID, it extracts and verifies the RFID data contained within the NFC chip. This verification process involves cross-referencing the information printed on the document.
NFC is particularly appealing for document and identity verification due to its high level of security. The chip within these documents contains identical biometric data as that on the physical document, including a digital, higher-resolution version of the photograph.
Many countries and states have NFC-enabled biometric passports, as well as biometric national identity cards and residence permits equipped with NFC capabilities. Regulators approve NFC-based verification as one of the Know Your Customer (KYC) compliance solutions.
The Stages of NFC-Based Verification
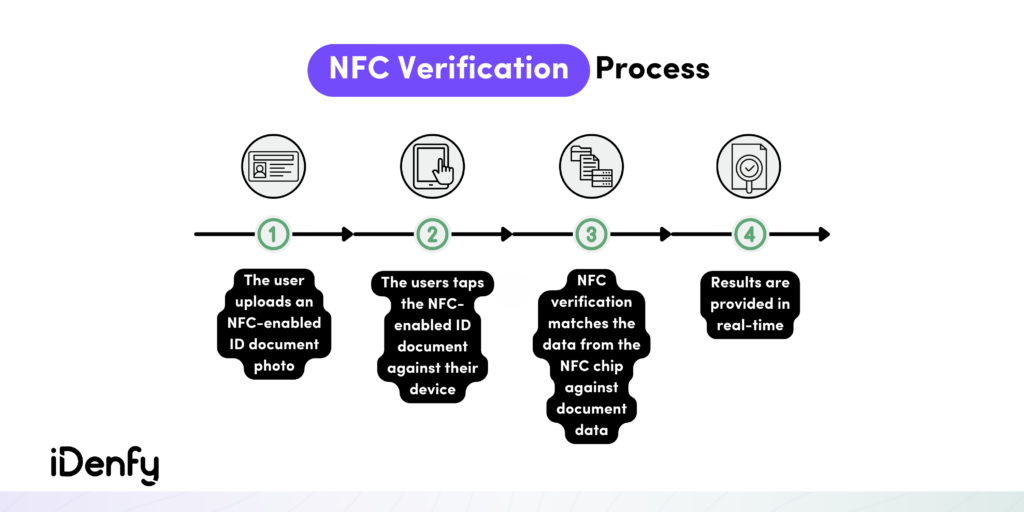
Here’s a step-by-step breakdown of the NFC-Based Verification process:
- The user takes a photo of their ID document.
- The verification system checks if the user’s phone and the ID document support NFC.
- The user then taps their phone against their ID.
- The ID verification software extracts personal data (such as name, document number, and issue date) from the NFC chip in the document.
- The system cross-checks this NFC-extracted data with the corresponding information obtained from the ID document picture.
At iDenfy, we offer a customized approach to NFC identity verification.
With our AI-powered ID verification software, you can combine NFC technology, 3D liveness detection, and human in-house expertise to benefit from accurate real-time verification. That also means you can choose how you want to build your verification flow.
Implement our NFC add-on for greater security, even in cases where standard ID verification is already enabled. Add NFC verification with face authentication, liveness detection, address verification, etc.
Countless options and complete compliance under one platform. Grab your demo today.