July 12, 2022
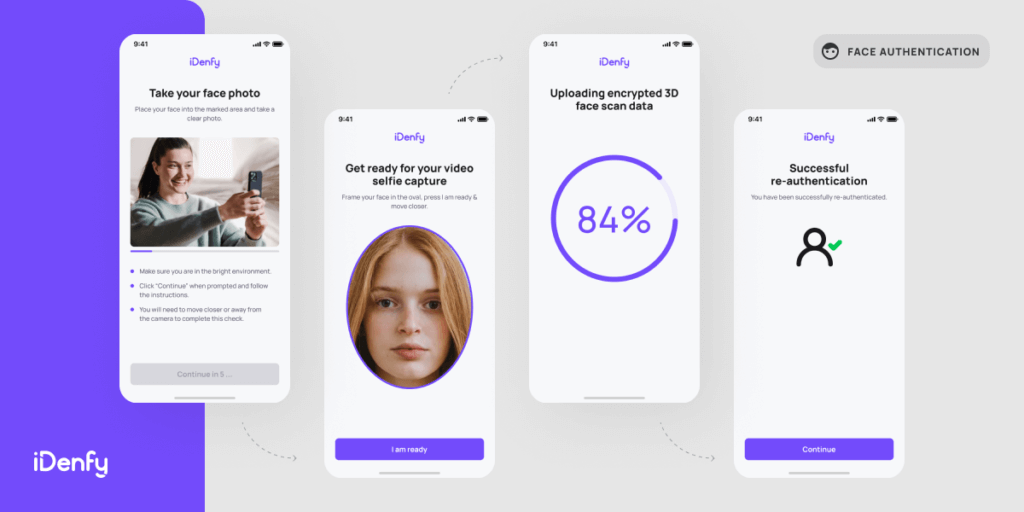
Improve KYC Process Using Face Authentication
iDenfy launches a face authentication toolkit to authenticate your existing customers by minimizing the account takeover threats There is a constant threat of account takeover to perform high-value transactions or change your sensitive account data. All of those actions should be secured using additional verification. Yet it has to be seamless and not make the […]

Know Your Business (KYB) Verification: What You Need to Know
Learn what Know Your Business, or KYB verification, is, focusing on the main compliance challenges in regulated, high-risk industries while learning about key automation solutions.

June 14, 2022
Deividas — the Backend Team Lead Who Dreamt of Being a Doctor
It’s that time of the month when we present our beloved team members! If you’ve been following us for a while now, you’ve met our other specialists: Gintarė, Viktor, and Raminta. We’re thrilled that our team is getting bigger and stronger. One of our goals is to welcome the best specialists into our family and […]
May 31, 2022
Identity Verification in the Art Market: KYC/AML Checklist to Prevent Fraud
While some use art to awaken their imagination or express themselves, others see it as a great way to invest. You can argue about the taste in art or what piece to put in your living room, but one thing’s for sure: art has always been a part of luxury and an entry into the elite. It also comes with a huge price tag and a possible risk factor. In this article, we discuss how identity verification helps combat fraud in the art market.

May 5, 2022
How to Create a Strong Password? [2025 Guide]
Is your password a minimum of 12 characters in length? Not only this, but also other important password factors determine the level of security.
April 21, 2022
Electronic Know Your Customer (eKYC) Explained
Explore the different benefits and opportunities that eKYC can bring to many industries and learn how to optimize compliance workflows.

April 12, 2022
Gintarė’s Guide To Leadership: Empathy Is Key
While many face different challenges at work, iDenfy strives to concentrate only on the positives. Of course, the major growth of the team proves that it’s working – we’ve almost doubled the number of our amazing colleagues in 2022. The bigger squad came with more responsibilities and opportunities. Today, we’re diving into another dedicated, hard-working […]
Screening and Ongoing Monitoring: Using AI Tools for AML Compliance
Are you wondering what tools and methods can detect and prevent vicious crimes, such as illegal earnings and money laundering? Will it be Customers’ AML Screening and Ongoing Monitoring? Keep reading to find out.

February 1, 2022
Presenting Viktor Vostrikov: One App, Big Responsibilities
iDenfy’s team has started to snowball in the past year. You might have already met my colleague – Raminta – and now, it’s my turn to tell the exciting story of how my journey at iDenfy began, and what it’s like to work in the diverse environment of the Fin-tech industry. I’m Viktor Vostrikov, and […]

January 25, 2022
Dangers of the Dark Web: How to Protect Yourself?
The internet is massive, with millions of websites, forums, servers, and databases that exchange information 24/7/365. But that’s only the “visible” side of the internet, which means that all these sites and servers can easily be found using Google and other search engines. This is the surface net, and below it is a different story about the dark web.

January 6, 2022
What is Phone Number Verification? A Complete Overview (2025)
Phone verification is the verification of a phone number through various methods such as making a phone call or sending a text message and receiving a response. Check out how leveraging different phone-related checks can help you determine customer risk profiles, verify their identities and deter fraud.

December 29, 2021
Highlights of 2021 – a Year of Growth For iDenfy
What a year! In 2021, iDenfy experienced a great number of exciting partnerships, attracted talented new members, reached a milestone in sales revenue, created various useful products, and received an assembly award for accomplishments in the identity verification world. The mission to stop fraud isn’t easy, but this year’s rapid growth showed that anything’s possible. […]

December 7, 2021
Raminta Bastikaitytė: Colorful, Punctual, Ambitious, and Motivated
The working environment at iDenfy is far from dull. But don’t just take our word for it – we’re here to introduce the perspectives of our employees. Raminta Bastikaitytė is the Head of the Verification Department at iDenfy. She will be the first to share about herself and her experience at the organization. Distinctive Hobbies […]