Today, we’re living in the digital world. Therefore, the importance of digital identity has increased several times than before. Nowadays, you can see that almost every business has started accepting digital identities, whether it’s a hotel, a bank, a telecom company, or an e-commerce site.
Digital identity is essentially your online representation, comparable to a driver’s license or ID card. It encompasses all the information that defines your identity. Unlike a physical ID card, acquiring a digital identity doesn’t involve any application or sign-up process. Anyone on the internet inherently possesses some form of digital identity.
However, when it comes to digital identity authentication, it’s not as straightforward as we see in the real world. Since users or customers are not physically present during the process, it’s not easy for companies to verify whether they have submitted legitimate information.
In this post, we explain digital identity, what can make it vulnerable, and how to protect it. So, without any further ado, let’s get started.
What is Meant by Digital Identity?
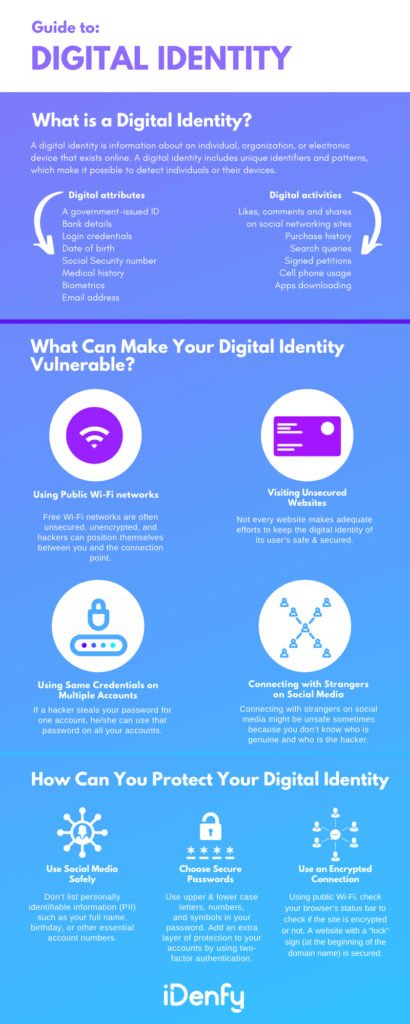
A digital identity is information about an individual or organization that exists online or is available in a digital form. It encompasses crucial details like your account names, browsing history, and even medical records. That’s why this information can be everything from your name to your date of birth to your social security number to even something less known, such as your likes on Instagram.
A digital identity includes unique identifiers and patterns, which make it possible to detect individuals. Digital identities are crucial for verifying who you are and preventing fraud. Safeguard your online identity by following basic cybersecurity measures like using a strong password, enabling two-factor authentication, or using other identity proofing techniques.
The information that completes your digital identity can be divided into two categories:
- Digital attributes
- Digital activities
Whether used individually or in combination, companies use these pieces of information to identify you, especially when it comes to security or compliance reasons in regulated industries, such as fintech.
Digital Attributes vs Digital Activities
Digital attributes are those parts of a digital identity that make it a complete digital identity. In contrast, digital activities are the records of something you do online.
1. Examples of digital attributes
- A government-issued ID (driver’s license, passport, etc.)
- Biometrics (eye scan, fingerprint, 3D face map)
- Login credentials (username and password)
- Bank details
- Date of birth
- Social Security number
- Medical history
- Email address
2. Examples of digital activities
- Purchase history
- Search queries
- Signed petitions
- Phone usage
- Downloading applications
- Likes, comments, and shares on social media sites
These examples represent sensitive Personally Identifiable Information (PII), which is safeguarded through user privacy services on apps or websites. While passwords and data encryption protect the most sensitive PII you share online, this doesn’t guarantee its safety.
Ensure your customers are real. Schedule a free demo here.
What Can Make Your Digital Identity Vulnerable?
Your digital identity can be exposed and fall into the wrong hands in several ways. Sometimes, cyber attackers use a unique method to steal our digital identity. Despite that, in most cases, we don’t take preventive measures and become an easy target of online fraudsters.
Let’s take a look at some possible scenarios for digital identity theft:
🟣 Using the Same Credentials on Multiple Accounts
Many people do this so that they don’t forget their passwords. However, they don’t realize that it can increase the risk of their account being compromised. God forbid, if a hacker steals your password for one account, they can use that password on all your accounts.
🟣 Using Public Wi-Fi networks
The data over public Wi-Fi is often unsecured and unencrypted. Hackers can position themselves on open, free Wi-Fi networks between you and the connection point. That’s why you should use such networks carefully.
🟣 Visiting Unsecured Websites
Not every website makes adequate efforts to keep the digital identity of its users safe and secure. If you often do online shopping or visit a marketplace that requires you to share your digital identity, make sure it is reputable and uses an SSL certificate.
🟣 Connecting with Strangers on Social Media
Connecting with strangers on social media might be unsafe sometimes because you don’t know who is genuine and who is the hacker.
🟪 Other Things That Can Make Your Digital Identity Vulnerable:
- Data breaches
- Unsecured mailbox
- Lost social security card or other government issued-ID
- Weak data protection
What is Digital Identity Theft?
Digital identity theft is a type of online fraud where a hacker pretends to be you, gaining access to your accounts and personal information or deceiving others. This is a significant threat because your digital identity is the key to numerous online services and is extensively used for verification.
Despite your knowledge of safeguarding against identity theft, your digital identity might be at risk. Understanding its security is crucial to ensure your safety, regardless of your online activity.
What Happens When Your Digital Identity Gets Hacked?
Digital ID theft is like a gold mine for cybercriminals. Depending on the type of information stolen, it can be used for a variety of purposes. Most of this information is sold in the underground market.
- Personal information such as name, DOB, address, phone number, and social security number can be used to apply for loans or credit cards under the user’s name. Moreover, such data is sold to marketing companies specializing in spam campaigns.
- Financial information, such as banking and insurance data, is used by hackers to access accounts and process fraudulent online transactions.
- The medical history of a patient encloses a large number of a user’s identifying information, which can be used for buying illegal and non-prescribed drugs.
- Leakage of educational information might expose users to extortion and blackmail. A blackmailer may utilize educational information to trick or scare users into fulfilling their demands.
- If cyber attackers steal your debit or credit card details, they might use it to make immediate purchases.
- If your user credentials, like your usernames and passwords, are exposed, your accounts might be used for phishing attacks and the perpetration of spam.
Fraud detection and prevention service from market leaders. Schedule a free demo here.
How Can You Protect Your Digital Identity?
1. Choose Secure Passwords
Make sure your passwords are secure. It’s advisable to use upper & lower case letters, numbers, and symbols in your password. Add an extra layer of protection to your accounts by using two-factor authentication.
2. Be Vigilant When Using Social Media
Always make sure your profiles don’t list PII, such as your full name, birthday, or other essential account numbers. Remember, the less information available to the public, your digital identity will be safer.
3. Use an Encrypted Connection
Avoid using public Wi-Fi and access only those websites that use encryption. You can see your browser’s status bar to check if the site is encrypted or not. A website with a “lock” sign (at the beginning of the domain name) is secured.
4. Update Security Software Timely
If you’re using security software, make sure they are timely updated. You should set the “Update” settings to automatic.
Every time you come across a service provider that needs your digital identity to offer its services, you must ensure that the provider has Secure Sockets Layer (SSL) certification and other security certifications.
Securing Digital Identities with iDenfy’s AI-Powered ID Verification Software
At iDenfy, we’re serious about meeting the highest standards for ISMA (Information Security Management Systems). As a leading identity verification service provider, we can’t take our clients’ security back seat.
We’re offering our advanced identity verification solutions to businesses and individuals across the globe to meet KYC/KYB compliance requirements, as well as other RegTech solutions to boost AML workflows.
Get started right away.
This blog post was updated on the 21st of December, 2023, to reflect the latest insights.