Undoubtedly, digital transformation has been bringing many benefits to the business world. It is helping individuals and businesses in improving their operations, resource management, customer reach, customer experience, and more. However, we can’t ignore that with the increase in technology, cybersecurity issues have also increased. Consequently, it’s getting tougher for businesses to establish trust online.
Fortunately, cybersecurity issues such as identity fraud and data breaches can be prevented and minimized to a great extent by enforcing a strict identification, verification, and authentication process within an organization. These three together can play a significant role in keeping your systems and resources safe from identity fraud.
Let’s find out what correctly these terms mean and how they can help you with identity verification and preventing identity theft.
Prevent and detect crime online faster with AI-powered identity verification
The complete ID verification takes up to 3 minutes or four steps
What is Identity Verification?
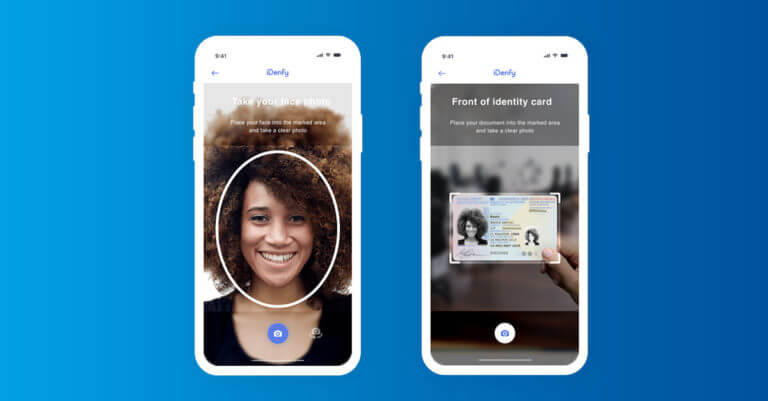
Identity verification is the process of proving that a person’s identity is genuine. Using ID verification, companies ensure that a customer is who they claim to be. In the world of AI and where technologies like ChatGPT are easily accessible, fraudsters easily forge identity documents or use fraudulent methods, like deepfakes, to bypass the verification process. That’s why this security measure is commonly used in financial activities, such as opening a bank account, and identity verification allows businesses and service providers to confidently engage with verified individuals.
Various ID verification solutions today allow companies to verify customers remotely, which means accepting new user registrations online. Building an automated IDV flow means accepting identities through document verification, an example of the Know Your Customer (KYC) measure. Using this type of ID verification, organizations accept government IDs or business licenses and then check the user’s personal information against authoritative databases. An alternative method would be to implement an extra selfie verification check, which requires users to take a photo of their face in order to have their biometrics verified.
Differences Between Identification, Verification, and Authentication

Identification is merely asking customers or users to present ID documents to prove who they are. In contrast, the verification process involves ensuring whether or not identity data is associated with a particular individual, for example, matching an individual’s date of birth to an individual’s name.
Identity authentication, on the other hand, takes verification to the next level and is exceptionally crucial while dealing with online transactions. In this process, a user or customer is asked for dynamic knowledge-based authentication (KBA) questions that are not easy to answer.
Need more clarification? Let’s explore each term in detail below.
What is Identification?
Identification is the process where someone claims to be a particular person by showing up a document that has his/her picture and personal information. A driver’s license is an excellent example of identification.
However, when it comes to online transactions, consumers identify themselves by entering their name, contact number, or email address on a web form. If users are buying something online, they have to provide their credit card details and billing address.
If you’re into a business where you think you don’t need to doubt your consumers or users, the identification process alone might work for you. For transactions that involve small amounts, it might be adequate to make someone declare their identification without confirming it. But as said above, identity-related frauds are on the rise; it’s advisable not to rely on identification alone. It will be like having a username without a password.
In the age of identity theft, you can’t be sure that the person you are interacting with is the person they are claiming to be. Consequently, verification is an important step. Let’s get to know what exactly is identity verification.
What is Verification?
As per the FTC’s Consumer Sentinel Network Data Book, identity theft, imposter scams, and debt collector frauds were the most common categories for fraud complaints in 2019. More than 167,000 people reported that their personal information had been used to open fraudulent credit card accounts. It merely shows that businesses need to go beyond the identification process in the current scenario.
Let’s find out what does the verification process involves:
Identification asks, “who are you?” but verification takes it one step further and asks, “are you actually whom you say you’re? The verification process is necessary to establish a reliable connection between a person who claims to be someone and who requires identity verification.
Usually, the verification process begins with the verification of government-issued ID documents. Human experts, automation data extraction, and machine learning technology are used to confirm whether the ID document is valid.
Verifying someone’s identity to such a high degree requires a lot of effort and knowledge of technology. Therefore, more and more businesses are looking for a professional identity verification service.
As private information of a person is readily available on the web nowadays, knowledge-based verification has become less reliable. Organizations that still depend on conventional methods of verifying an identity run the risk of loss via the fraudulent activities of cybercriminals.
Although ID verification is essential for all types of businesses, you must verify your customers’ and clients’ identities if you’re into financial services, online marketplace, travel, insurance, and real estate business.
The game-changing experience with iDenfy’s biometric identity verification
Once you try it, you can’t go back
What is Authentication?
Identity verification is conducted only once. Once verified, the identification of a person must be authenticated each time they try to get access to your resources and system. In the authentication process, users are asked to re-confirm if they are the same people who have registered.
In low-risk businesses, identity authentication can be as simple as asking for the password for a specific username along with a security question. The majority of authentication systems depend on the three types of authenticators that include:
- Something, the customer, knows, for example, a password or security question.
- Something, the customer, has such as a cryptographic key or ID badge.
- Something, the customer, is, for instance, biometric data and facial recognition.
Unfortunately, the first two forms of authentication are not considered that much secure in today’s scenario as people’s private information is available on social media sites, forums, and other sources available on the internet. Cyber attackers can use this data to get access to your system.
So to be ensured you’re granting permission to the right person, you must look for advanced real-time identity verification.
Changes in Approaches to Identity Verification and Authentication
As cybercriminals are changing their attack strategies, changes in approaches to identity verification and authentication are also necessary. To strengthen your identity theft protection, you must combine identity documentation and biometric recognition technology.
If you’re looking for advanced identity verification solutions for your business, you can rely on iDenfy. We help you make your identity recognition process smooth and straightforward.
At iDenfy, we pride ourselves on providing next-generation identity verification technologies that include liveness detection, facial recognition, ID verification, and more.
We provide KYC, KYB and AML solutions in one, unique platform, offering customized workflows and white-label options tailored to your industry. Get a hands-on tour for free here.

This blog post was updated on the 30th of May, 2024, to reflect the latest insights.